What is Keylogger?
Quick Summary: This article provides a comprehensive guide on safeguarding against keylogger. It covers its various types, functions, and real-world impact that help readers understand and defend against privacy-threatening software.
Introduction
Cyber threats today go beyond traditional malware in today’s interconnected digital world. In recent years, keyloggers have gained notoriety as covert threats.
Some cyber threats seem straight out of a spy movie or sci-fi movie. Nevertheless, they are true; you are their target, even if you don’t know it yet. Keylogger attacks are among the malware exploits they use to exploit vulnerabilities. Many trusted software development services employ keyloggers to protect their data.
This comprehensive article aims to help you defend against keyloggers by explaining their types, mechanisms, and actual effects.
What Is Keylogger?
A keylogger is a malicious software or hardware that records and tracks keystrokes on a computer or device. Furthermore, keyloggers can capture confidential data such as credit card numbers, passwords, and personal messages without the user’s knowledge, causing a significant threat to security.
Types of keyLogger
There are two types of key-Logger
1. Software-based keyloggers
- A software-based keylogger is a type of malicious program that captures unauthorized data theft.
- Some of these features include:
- Logging of the clipboard: The software can capture anything copied to the clipboard.
- Logging on the computer screen. It is necessary to take screenshots to collect graphics-based information.
- Capturing text in a control programmatically.
- Records information such as search engine queries, instant messenger talks, FTP downloads, and other Internet-based activities.
2. Hardware-based keylogger
- Typical Hardware Keylogger is a hardware circuit that is installed anywhere between the computer keyboard and the computer for keystroke logging.
- Hardware keyloggers have an advantage over software keyloggers in that they can start logging as soon as the machine is switched on.
- Hardware-based keyloggers do not require the installation of any software because they operate at the hardware level of a computer system.
- A hardware keylogger’s memory size can range from a few kilobytes to several terabytes, with each keystroke recorded typically consuming a byte.
- Example
- USB Drive
- Cable Through


Anti-keylogger
An anti-keylogger is a piece of software specifically designed to detect keyloggers on a computer.
- One-time passwords (OTP)
- Security tokens
- On-screen keyboards
- Handwriting recognition and mouse gestures
- Deceptive typing
- Live CD/USB
- Step 1:
- Install software keylogger.
- Step 2:
- Open the software keylogger by pressing the following key. You can also change the key in settings. And Enter the password.
- Ctrl+alt+shift+key
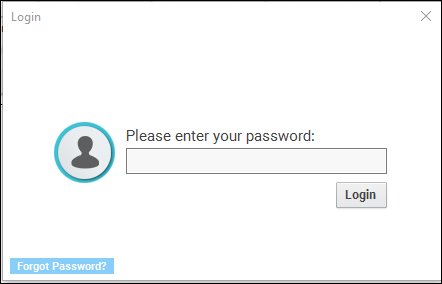
- Step 3:
- Main Dashboard will appear.
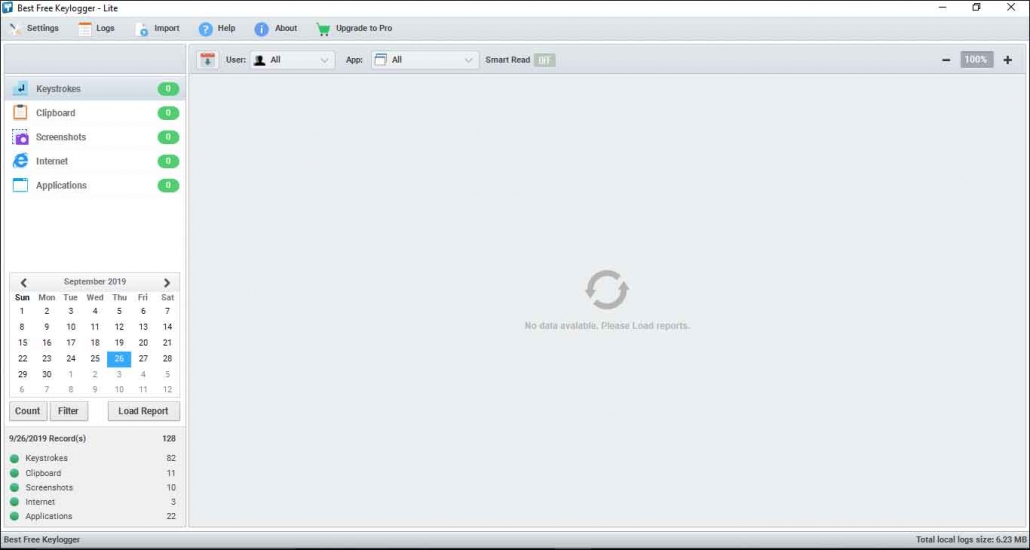
Functions of Keylogger
1. Monitoring
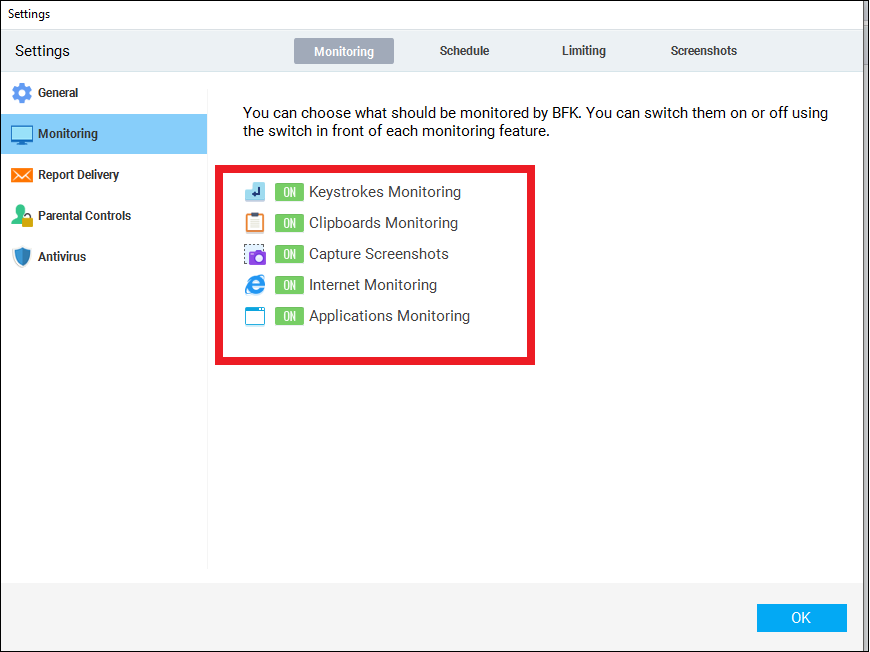
- After clicking on the Setting -> Monitoring tab following screen will appear.
- Make sure that all buttons are set to ON.
2. Report Delivery
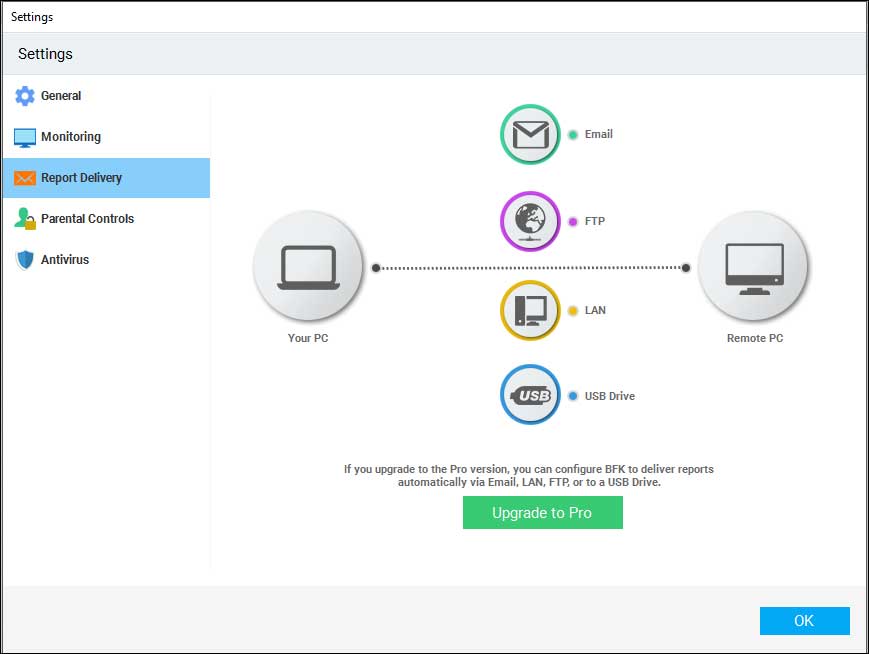
- We can also get the report from one system to another system.
- For that go to Settings-> Report Delivery.
3. Parent control
- It is very helpful for a parent to control their child’s system.
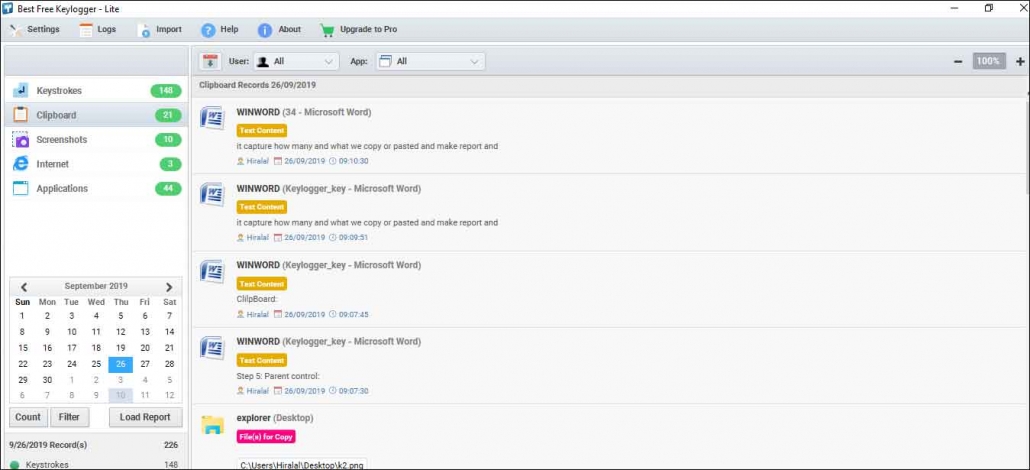
4. Clipboard
- It captures how many and what we copy or pasted It generates a report and displays it on the clipboard screen
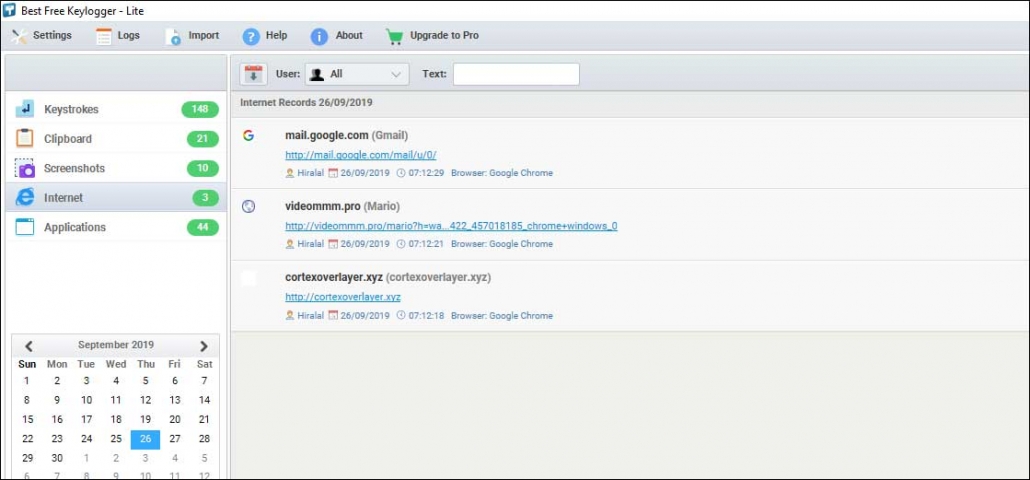
5. Internet
- It displays how many websites we visited with date & time.
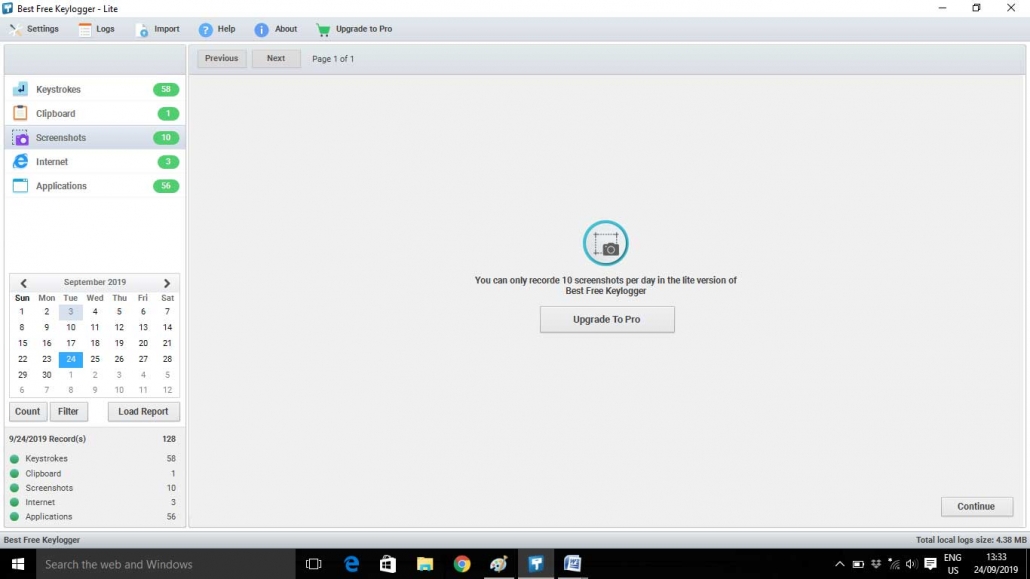
6. Screenshots
- It displays the total screenshot taken by the user.
7. Applications
-
- It displays the applications that we had used.
>
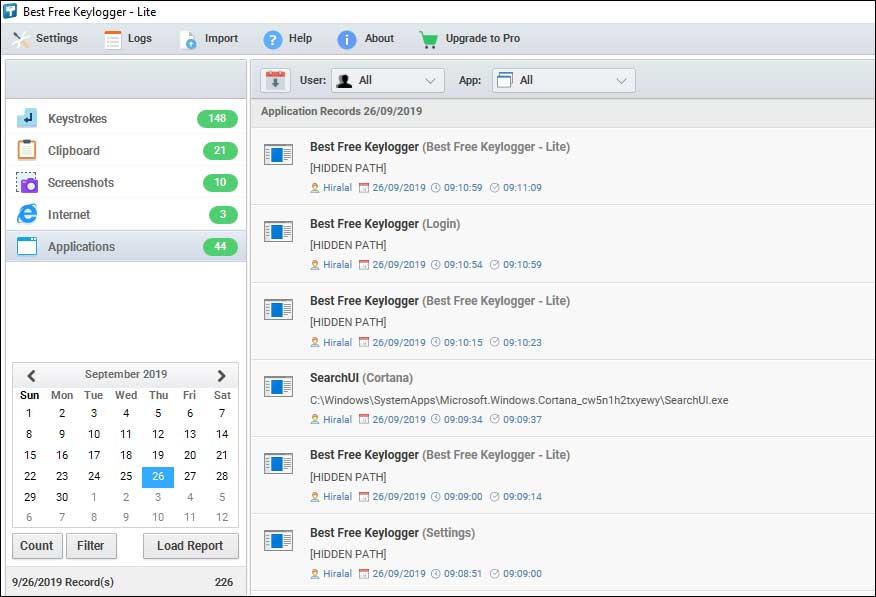
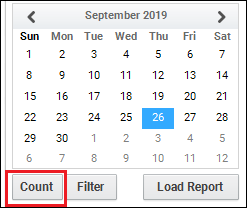
8. Count
-
- Display summary of user activities.
>
9. Filters
-
- If we need any specific type of data then we can get it from Filter.
>
How Keyloggers Work
Keyloggers play the same role, although they are spread in different ways. Furthermore, Keyloggers record all the information you enter into your device and convey the same to the recipients.
Below, we highlighted a few examples that will help you understand how keyloggers work:
Web page scripts
Hackers add a malicious code to your web page. Furthermore, when the user opens that infected link or enters a malicious webpage, the keylogger will automatically get downloaded to your system
Phishing
Hackers can use phishing emails fraudulent messages designed to look legitimate. When you click an infected link or open a malicious attachment, the keylogger downloads on your device.
Social engineering
Phishing is to trick victims into divulging confidential information, a form of social engineering. Furthermore, cybercriminals pretend to be trusted contacts to convince recipients to download malware or open an attachment.
Downloaded software that cannot be identified.
Internet users can embed keyloggers in software they download from the internet. Unknowingly, whenever you download software, you also download keylogging software.
Conclusion
The blog above serves as an insightful resource for comprehending the intricacies of keyloggers. By exploring their types, mechanisms, and real-world implications, you can mitigate the risks of these privacy-compromising tools.
FAQ
What is Keylogger logging?
A keylogger logs keystrokes on a computer or device, recording text input. Furthermore, it is helpful for various purposes, including monitoring or unauthorized data collection.
How do keyloggers work?
Keylogger works by capturing and recording keystrokes from a Keyboard. They can be hardware or software-based, covertly collecting typed information, which the attacker can access for malicious purposes.
Explain the keylogger malware definition.
Keyloggers are programs that record computer keystrokes using malicious software. Furthermore, it captures sensitive information such as passwords and credit card details, often for illicit purposes like identity theft.
Is keylogger a spyware?
A key logger is a form of spyware that records every keystroke you make and then sends it to a server, where you can retrieve log-in information, including your password.
Are keyloggers Trojan?
An anti-virus program that records keystrokes is called a keylogger Trojan virus. Computer infections are dangerous because they record every keystroke you make on your keyboard, including passwords and usernames.













